|
For the latest stable version, please use Spring Security Kerberos 2.2.0! |
Spring Security Kerberos Samples
This part of the reference documentation is introducing samples projects. Samples can be compiled manually by building main distribution from github.com/spring-projects/spring-security-kerberos.
|
If you run sample as is it will not work until a correct configuration is applied. See notes below for specific samples. |
Security Server Windows Auth Sample sample for Windows environment
Security Server Side Auth Sample sample using server side authenticator
Security Server Spnego and Form Auth Sample sample using ticket validation with spnego and form
Security Server Spnego and Form Auth Xml Sample sample using ticket validation with spnego and form (xml config)
Security Client KerberosRestTemplate Sample sample for KerberosRestTemplate
Security Server Windows Auth Sample
Goals of this sample:
-
In windows environment, User will be able to logon to application with Windows Active directory Credential which has been entered during log on to windows. There should not be any ask for userid/password credentials.
-
In non-windows environment, User will be presented with a screen to provide Active directory credentials.
server:
port: 8080
app:
ad-domain: EXAMPLE.ORG
ad-server: ldap://WIN-EKBO0EQ7TS7.example.org/
service-principal: HTTP/[email protected]
keytab-location: /tmp/tomcat.keytab
ldap-search-base: dc=example,dc=org
ldap-search-filter: "(| (userPrincipalName={0}) (sAMAccountName={0}))"In above you can see the default configuration for this sample. You
can override these settings using a normal Spring Boot tricks like
using command-line options or custom application.yml file.
Run a server.
$ java -jar sec-server-win-auth-2.0.1.jar|
You may need to use custom kerberos config with Linux either by using
|
|
See Setup Windows Domain Controller for more instructions how to work with windows kerberos environment. |
Login to Windows 8.1 using domain credentials and access sample
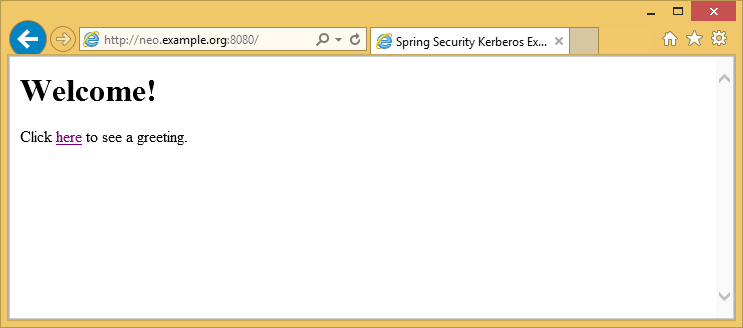
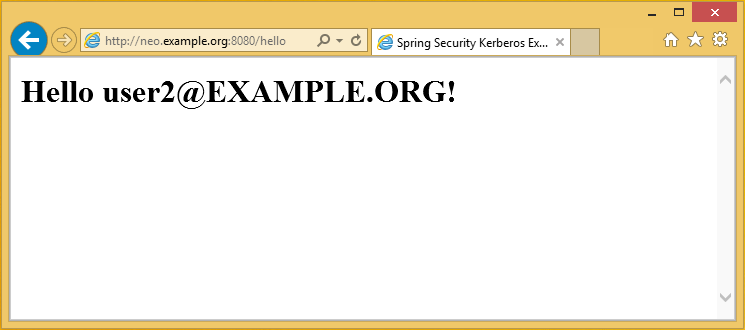
Access sample application from a non windows vm and use domain credentials manually.
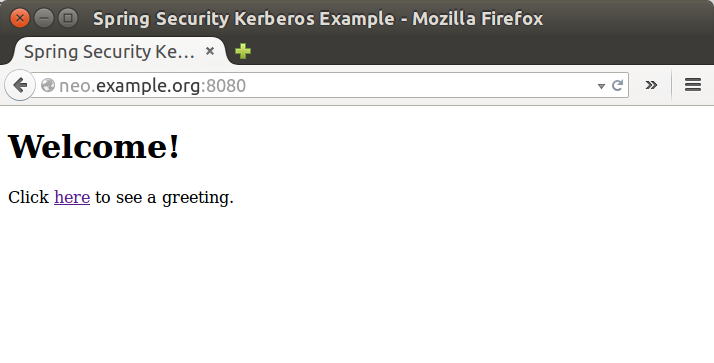
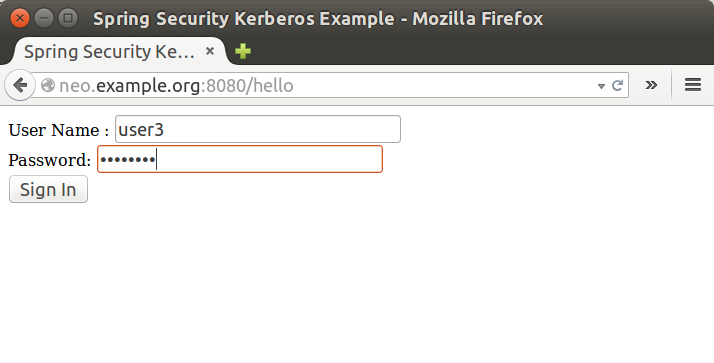
Security Server Side Auth Sample
This sample demonstrates how server is able to authenticate user against kerberos environment using his credentials passed in via a form login.
Run a server.
$ java -jar sec-server-client-auth-2.0.1.jarserver:
port: 8080Security Server Spnego and Form Auth Sample
This sample demonstrates how a server can be configured to accept a Spnego based negotiation from a browser while still being able to fall back to a form based authentication.
Using a user1 principal Setup MIT Kerberos,
do a kerberos login manually using credentials.
$ kinit user1
Password for [email protected]:
$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: [email protected]
Valid starting Expires Service principal
10/03/15 17:18:45 11/03/15 03:18:45 krbtgt/[email protected]
renew until 11/03/15 17:18:40or using a keytab file.
$ kinit -kt user2.keytab user1
$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: [email protected]
Valid starting Expires Service principal
10/03/15 17:25:03 11/03/15 03:25:03 krbtgt/[email protected]
renew until 11/03/15 17:25:03Run a server.
$ java -jar sec-server-spnego-form-auth-2.0.1.jarNow you should be able to open your browser and let it do Spnego authentication with existing ticket.
|
See Configure Browsers for Spnego Negotiation for more instructions for configuring browsers to use Spnego. |
server:
port: 8080
app:
service-principal: HTTP/[email protected]
keytab-location: /tmp/tomcat.keytabSecurity Server Spnego and Form Auth Xml Sample
This is a same sample than Security Server Spnego and Form Auth Sample but using xml based configuration instead of JavaConfig.
Run a server.
$ java -jar sec-server-spnego-form-auth-xml-2.0.1.jarSecurity Client KerberosRestTemplate Sample
This is a sample using a Spring RestTemplate to access Kerberos protected resource. You can use this together with Security Server Spnego and Form Auth Sample.
Default application is configured as shown below.
app:
user-principal: [email protected]
keytab-location: /tmp/user2.keytab
access-url: http://neo.example.org:8080/helloUsing a user1 principal Setup MIT Kerberos,
do a kerberos login manually using credentials.
$ java -jar sec-client-rest-template-2.0.1.jar --app.user-principal --app.keytab-location|
In above we simply set |
If operation is succesfull you should see below output with [email protected].
<html xmlns="http://www.w3.org/1999/xhtml"
xmlns:sec="http://www.thymeleaf.org/thymeleaf-extras-springsecurity3">
<head>
<title>Spring Security Kerberos Example</title>
</head>
<body>
<h1>Hello [email protected]!</h1>
</body>
</html>Or use a user2 with a keytab file.
$ java -jar sec-client-rest-template-2.0.1.jarIf operation is succesfull you should see below output with [email protected].
<html xmlns="http://www.w3.org/1999/xhtml"
xmlns:sec="http://www.thymeleaf.org/thymeleaf-extras-springsecurity3">
<head>
<title>Spring Security Kerberos Example</title>
</head>
<body>
<h1>Hello [email protected]!</h1>
</body>
</html>